A crafty new breed of social engineering attack is tricking users into launching malware straight from their clipboard, exposing a fresh vulnerability in Windows that even tech pros could fall for. Leo Laporte and Steve Gibson break down how the latest ClickF…
A crafty new breed of social engineering attack is tricking users into launching malware straight from their clipboard, exposing a fresh vulnerability in Windows that even tech pros could fall for. L… [+1627 chars]
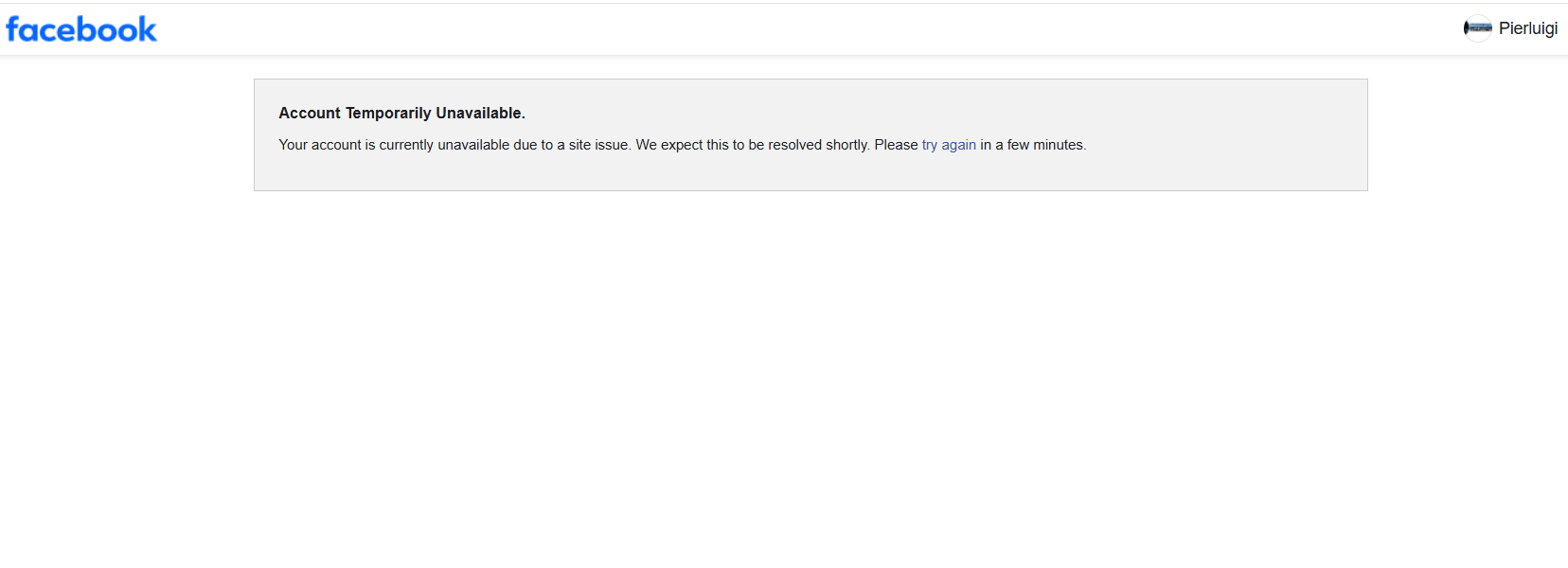
Facebook is experiencing a global outage since 4:15 PM ET, with users reporting they cannot access their accounts. Facebook users worldwide report problems while attempting to access their accounts. The outage started around 4:15 PM ET. Upon attempting to acc…
Facebook is experiencing a global outage
Facebook users worldwide report problems while attempting to access their accounts. The outage started around 4:15 PM ET. Upon attempting to access their acc… [+770 chars]
iVerify has described the activity as the “first known mass iOS attack” campaign of its kind. Google said fragments of the exploit first appeared last February, with ties to an unnamed “customer of a surveillance company.”
A powerful iPhone hacking toolkit that researchers say may have originated as a U.S.-built capability has surfaced in the hands of foreign espionage actors and financially motivated criminal groups, … [+4108 chars]
Zed is a high-performance, multiplayer code editor from the creators of Atom and Tree-sitter.
Last Updated: March 2, 2026
Welcome, and thank you for your interest in Zed Industries, Inc. (Zed, we, or us) and our website at www.zed.dev, along with our downloadable Zed software (the Software) … [+39516 chars]
The small volunteer-run club in Sydney's Sutherland Shire says the sudden hike will force it to close its doors.
A Sydney community sailing club is facing closure after NSW Crown Lands increased their annual land use fee by 648 per cent.
Port Hacking Open Sailing Club in Sydney's Sutherland Shire usually pays … [+3303 chars]
The Republic of Ireland suffered an agonising 2-1 defeat to France in their opening World Cup qualifier at Tallaght Stadium tonight, cursing the gods after a remarkable climax.
The Republic of Ireland suffered an agonising defeat to France in their opening World Cup qualifier at Tallaght Stadium tonight, cursing the gods after a remarkable climax.
Katie McCabe put the host… [+5643 chars]
Seven high-profile claimants allege the Daily Mail's publisher committed "grave breaches of privacy" - something it denies.
The claimants, which include Prince Harry, have accused ANL of "clear, systematic and sustained use of unlawful information gathering" for stories between 1993 and "beyond" 2018, including through pr… [+32 chars]
The foul shooting became a hot-button topic in last year’s playoffs.
TORONTO Mitchell Robinson isnt going to shoot his free throws underhand. In his view, form isnt the problem and granny style is silly as hell.
The issue, as Robinson laid out Tuesday, is the lack of… [+4275 chars]
The foul shooting became a hot-button topic in last year’s playoffs.
TORONTO Mitchell Robinson isnt going to shoot his free throws underhanded. In his view, form isnt the problem and granny style is silly as hell.
The issue, as Robinson laid out Tuesday, is the lack … [+4441 chars]
It seems a bit fishy that any intelligence agency would tip their hat and reveal the tactics used to assassinate a world leader.
There seems to be a bit of credit-taking going on, as some reports like those from The Times of Israel claim it was Mossad's camera-hacking intelligence that led to the strike. While others like the … [+1161 chars]
A highly sophisticated set of iPhone hijacking techniques has likely infected tens of thousands of phones or more. Clues suggest it was originally built for the US government.
Google notes that Apple patched vulnerabilities used by Coruna in the latest versions of its mobile operating system, iOS 26, so its exploitation techniques are only confirmed to work against iOS 13 … [+3903 chars]
While many Canadians are still waiting for the fastest 5G signals, Ottawa is already looking toward the next generation. At Mobile World Congress in Barcelona today, the federal government teamed up with global partners to lay out the ground rules for 6G secu…
While many Canadians are still waiting for the fastest 5G signals, Ottawa is already looking toward the next generation. At Mobile World Congress in Barcelona today, the federal government teamed up … [+2329 chars]
After U.S. and Israeli forces started bombing Iran, reports say cyber operations have disrupted communications, supporting surveillance activities, and have been used in psychological operations.
On Saturday, U.S. and Israeli jets began a bombing campaign against Iran, killing its supreme leader Ali Khamenei and several senior government officials. The attacks also hit military and civilian t… [+3784 chars]
If you suspect your job is in jeopardy, there are steps you can take — and mistakes you must avoid. Find out more.
You show up to work every day, thinking your position is secure. The truth? It isnt. Canadian workers are nervous, companies are cutting back and industries from tech to finance are being disrupted f… [+5012 chars]
Description: Avast Premium Security is an Avast product that offers antivirus protection and advanced security for your PC against online threats. It allows users to safely shop and bank online, avoid fake websites and phishing scams, block web spies, and mor…
Description: Avast Premium Security is an Avast product that offers antivirus protection and advanced security for your PC against online threats. It allows users to safely shop and bank online, avoi… [+3164 chars]
If you want clarity about someone’s online behavior, learning how to track someone on Instagram often starts when you notice changes in posting patterns, hidden stories, or sudden follower shifts. Instagram has over 500 million daily active story users, and …
If you want clarity about someones online behavior, learning how to track someone on Instagram often starts when you notice changes in posting patterns, hidden stories, or sudden follower shifts.
I… [+14490 chars]
Cloudflare Threat Report warns that AI tools enable attackers who lacked required skills to generate effective attacks rapidly and at scale
Easy access to large language models (LLMs) and other AI tools has significantly lowered the barrier to entry for cybercriminals to conduct effective cyber-attacks rapidly and at scale, a new threat … [+2857 chars]
Israel spent years hacking Tehran’s traffic cameras, monitoring guards before the assassination
When the highly trained, loyal bodyguards and drivers of senior Iranian officials came to work near Pasteur Street in Tehran where Ayatollah Ali Khamenei was killed in an Israeli air strike on Saturd… [+11300 chars]
Law enforcement data shows profit-driven cybercrime is dominated by 35- to 44-year-olds, not script kiddies Contrary to what some believe, cybercrime is not a kids' game. Middle-aged adults, not teenagers, now make up the biggest chunk of people getting buste…
Contrary to what some believe, cybercrime is not a kids' game. Middle-aged adults, not teenagers, now make up the biggest chunk of people getting busted.
That's according to new analysis of 418 publ… [+2903 chars]
A lot of making goes on in this community these days, but sometimes you’ve just gotta do some old fashioned hacking. You might have grabbed an old Speak and Spell that you want to repurpose a…
A lot of making goes on in this community these days, but sometimes you’ve just gotta do some old fashioned hacking. You might have grabbed an old Speak and Spell that you want to repurpose as an int… [+7059 chars]
Josys has transitioned into an autonomous identity governance platform, expanding beyond traditional SaaS management. The enhanced platform empowers IT leaders and managed service providers (MSPs) to scale governance and compliance efforts by centralizing ide…
Josys has transitioned into an autonomous identity governance platform, expanding beyond traditional SaaS management. The enhanced platform empowers IT leaders and managed service providers (MSPs) to… [+3249 chars]
Preface. The founder of the War on Drugs in the U.S., Harry Anslinger, wanted to build as large a bureaucracy as possible. But a war on narcotics alone—cocaine and heroin, outlawed in 1914—wasn’t enough. They were used only by a … Continue reading →
Source: Tim Kelly
Preface. The founder of the War on Drugs in the U.S., Harry Anslinger, wanted to build as large a bureaucracy as possible. But a war on narcotics alonecocaine and heroin, outlawed … [+72264 chars]
Europol’s Project Compass targets The Com (aka 764 network), an online group exploiting minors. After 30 arrests, officials say the hunt for those involved is far from over.
A massive international police effort has finally revealed the truth about The Com (also known as 764), a dangerous online network that has been quietly threatening young people across the globe. Kno… [+4289 chars]
Israeli spies spent years hacking nearly every traffic camera in Tehran so they could monitor Iranian Supreme Leader Ayatollah Ali Khamenei before he was eventually wiped out, according to a report.
Israeli spies spent years hacking nearly every traffic camera in Tehran so they could monitor Iranian Supreme Leader Ayatollah Ali Khamenei before he was eventually wiped out, according to a report.
… [+1724 chars]
Inside the accidental digital revolution where compliance becomes competitive advantage, AI kills SEO, and speaking Dutch pays better than Silicon Valley tactics
Belgiums 1.98 Billion Digital Ad Revolution: How Shopify, Bancontact, and Brussels Bureaucrats Built Europes Weirdest Marketing Goldmine
Plus: Why your startups growth strategy is about to become ex… [+11165 chars]